Lewis Woodcock recalled during a keynote address how he walked through the offices of the company in late June 2017 and saw row after row of blank screens during business hours. Woodcock was head of cybersecurity compliance at Moller-Maersk, the world’s largest container shipping firm.
“There was a moment of disbelief, initially, at the sheer ferocity and the speed and scale of the attack and the impact it had,” he said. The NotPetya ransomware had disabled 50,000 infected computers and thousands of applications and servers across 600 sites in 130 countries. Moller-Maersk estimates it alone lost $300 million due to operational stoppages. Its business dipped 20-percent during the months it took to bring its systems online.
Ransomware is software that locks users out of their data by encrypting the information. The user requires a special key-code to retain access to their data. Only the hacker has the key, though, which a business must pay to acquire. The most malicious ransomware erases all of a user’s data, whether the victim pays the ransom or not.
Whether organizations should pay ransom to hackers is a difficult one to answer. Nevertheless, enterprises at the Board level need to have the debate, while executives need to map out ahead of such an event what the business’s response should be.
How Prevalent is Ransomware?
Corporate extortion and ransomware were listed as the “most significant risks to businesses” by 72 percent of respondents in a global survey of 900 CIOs by Logicalis. Europol’s 2018 Internet Organised Crime Threat Assessment saw an increasing trend in the frequency of cyber extortion.
The FBI calculates a ransomware attack occurs in the United States every 14 seconds, with 4000 crimes of this sort occurring daily since 2016.
“It’s less of an individual user, and it’s more targeting towards the private sector, businesses, or public sector, municipalities, police departments, etc. Those attacks are going up, while attacks on individual users are going down,” Lawson told CNN.
Who Is Behind the Attacks?
The culprits behind corporate and local government ransomware attacks are not kids in their bedrooms. Instead, many of the attacks come from criminal organizations and nation-states. For instance, the Department of Justice indicted two Iranian nationals for a series of ransomware attacks with malware named SamSam. The incident caused $30 million in damage to municipalities, hospitals, and schools in 2015.
In 2017, law enforcement officials across six federal agencies arrested three Eastern Europeans for ransomware attacks on businesses.
To Pay or Not to Pay?
With the spike in ransomware attacks on local governments, many mayors have chosen to pay ransoms, including Lake City and Riviera City in Florida. Lake City paid a $460,000 ransom, while Riviera City paid $600,000. Payments, however, have not deterred ransomware activity overall. Recorded Future reported a spike in ransomware attacks targeting US cities. Recent victims have included Atlanta, Georgia, Lynn, Massachusetts, Cartersville, Georgia, and Baltimore, Maryland.
Atlanta and Baltimore refused to pay the ransoms. Instead, they chose to spend millions of dollars on the sorts of IT infrastructure upgrades that would mitigate future attacks. Nevertheless, it is still unclear whether it is in the organization’s best interest to pay ransoms.
Forrester Research has suggested in a report that paying ransom may become a viable option for businesses under certain circumstances. Organizations need to compare the cost of not being able to operate with the expense of decrypting the ciphers that hackers used to lock up computers on the network. Typically, the exercise requires hiring expensive outside experts to invest days in cracking the codes.
Further, if companies proceed with the Do-It-Yourself decryption option, they have no assurance that their systems will have the same capabilities as before the attack. Executives may also discover during an attack that some corporate insurance policies may not cover ransomware incidents. Also, the criticality of some datasets may make it necessary for companies to reacquire control of their systems quickly.
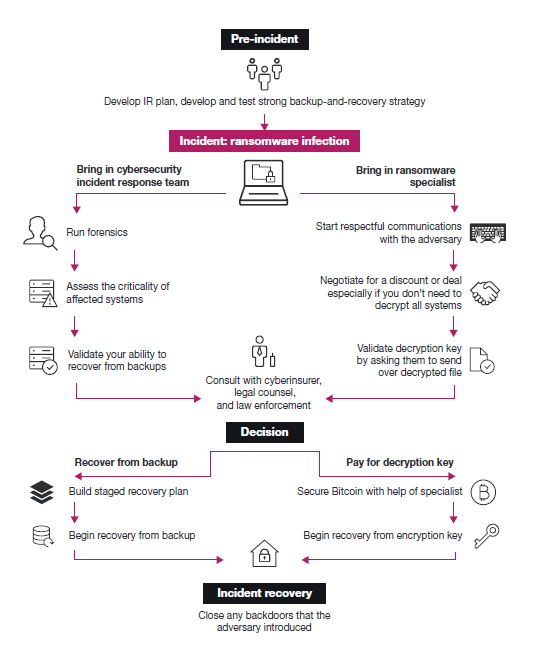
Source: Forrester Research
Nevertheless, organizations need to make sure they back up all critical systems frequently, Forrester recommends. They also need to know ahead of time how to obtain cryptocurrency, the favored currency of hackers. It’s also a wise decision for businesses to arrange a retainer for a ransomware response team. The team should include a negotiator who may be able to negotiate a lower price to unlock the workstations.
Unfortunately, as more organizations pay ransoms, cybercriminals will find the hack a lucrative way to make money, encouraging more commercial crimes of this sort.
Ransomware attacks are the new normal for business and government operations.